All-in-One PicoCTF Writeups: Forensics

All-in-One PicoCTF Writeups: Forensics
S1l3ntC0nquerPreface
In fact, there seems to be nothing to say about the preface, but I just don’t want to classify the topics at the beginning, so I still put a preface XD.
When I was brushing PicoCTF, I often found that almost all writeups were in English, so I wanted to write a more complete Gujarati version! In short, I will try my best to collect all the picoCTF questions here (but because I have already written about 60 questions before I start to write writeup, I may wait for the other parts to be completed before filling in the previous part), if necessary You can just come here to see all the writeups, that’s it! Hope this helps.
#MSB
Judging from the title of this topic and its appearance in Forensics, it should be related to steganography. If you still don’t know what LSB and MSB are, you can first read [Cryptography Notes: The Meridian of Cryptography](https://s1l3ntc0nquer.github.io/web/Notebooks/Cryptography-Notebook-: The Meridian of Cryptography/) , which explains what LSB and MSB are.
The title of the question says, This image passes LSB statistical analysis. On the contrary, it actually implies that the flag may be hidden in the MSB of the RGB pixel value, so let’s extract the MSB of each pixel. The Pillow library in Python is used here. If you find it too troublesome, you can also directly use this ready-made tool Stegsolve.
The exploit is as follows:
from PIL import Image
import re
def extract_msb(image_path):
image = Image.open(image_path)
pixels = image.load()
# Get image size
width, height = image.size
# Initialize and store the string extracted from MSB
msb_data = ""
#Extract the MSB of each pixel
for y in range(height):
for x in range(width):
r, g, b = pixels[x, y]
# The AND operation only retains the highest bits of r, g, and b, then clears them to zero, and then shifts them to the right by 7 bits.
msb_data += str((r & 0b10000000) >> 7)
msb_data += str((g & 0b10000000) >> 7)
msb_data += str((b & 0b10000000) >> 7)
#Convert every 8 bits of the extracted MSB into characters
hidden_text = ""
for i in range(0, len(msb_data), 8):
byte = msb_data[i : i + 8]
if len(byte) == 8:
hidden_text += chr(int(byte, 2))
return hidden_text
def find_pico_ctf(data):
pattern = r"picoCTF\{.*?\}"
matches = re.findall(pattern, data)
if matches:
for match in matches:
print(f"Found: {match}")
else:
print("No matches found")
if __name__ == "__main__":
image_path = (
"MSB/Ninja-and-Prince-Genji-Ukiyoe-Utagawa-Kunisada.flag.png" # Replace with your path
)
hidden_message = extract_msb(image_path)
find_pico_ctf(hidden_message)picoCTF{15_y0ur_que57_qu1x071c_0r_h3r01c_ea7deb4c}#Verify
First connect to the host given in the question.
Then use ls to see what files are there.
ctf-player@pico-chall$ ls
checksum.txt decrypt.sh filesThe title says that decrypt.sh is a script used to decrypt files, checksum.txt is a file that records the correct hash value, and finally files is a directory with many files in it, but only one can be used to be Correct script for decryption. So what we have to do is compare the hash value of each file with the value of checksum.txt. We use the following two commands to first use cat to get the correct hash value, then use sha256sum to calculate the hash of each file in files, and finally compare.
ctf-player@pico-chall$ cat checksum.txt
5848768e56185707f76c1d74f34f4e03fb0573ecc1ca7b11238007226654bcda
ctf-player@pico-chall$ sha256sum files/* | grep 5848768e56185707f76c1d74f34f4e03fb0573ecc1ca7b11238007226654bcda
5848768e56185707f76c1d74f34f4e03fb0573ecc1ca7b11238007226654bcda files/8eee7195The last line of Show shows that the correct file is 8eee7195, then use ./decrypt.sh to decrypt it. Just get Flag.
picoCTF{trust_but_verify_8eee7195}#CanYouSee
After decompressing the Handout of this question, there is a picture. I first tried steghide to extract the steganographic information, but what was extracted was the following.
The flag is not here maybe think in simpler terms. Data that explains data.Data that explains data. This tells us to look for his Metadata. Use the following command here.
exiftool ukn_reality.jpgThe result after execution is:
ExifTool Version Number : 12.76
File Name: ukn_reality.jpg
Directory: .
File size: 2.3 MB
File Modification Date/Time: 2024:03:11 20:05:53-04:00
File Access Date/Time: 2024:09:01 13:25:54-04:00
File Inode Change Date/Time: 2024:09:01 13:25:46-04:00
File Permissions: -rw-r--r--
File Type: JPEG
File Type Extension: jpg
MIME Type: image/jpeg
JFIF Version: 1.01
Resolution Unit: inches
Resolution: 72
Resolution: 72
XMP Toolkit : Image::ExifTool 11.88
Attribution URL : cGljb0NURntNRTc0RDQ3QV9ISUREM05fYjMyMDQwYjh9Cg==
Image Width: 4308
Image Height: 2875
Encoding Process: Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components: 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size: 4308x2875
Megapixels: 12.4The Attribution URL looks suspicious, base64 decode it.
base64 -d <<< cGljb0NURntNRTc0RDQ3QV9ISUREM05fYjMyMDQwYjh9Cg==Sure enough, I got Flag.
picoCTF{ME74D47A_HIDD3N_b32040b8}#Secret of the Polyglot
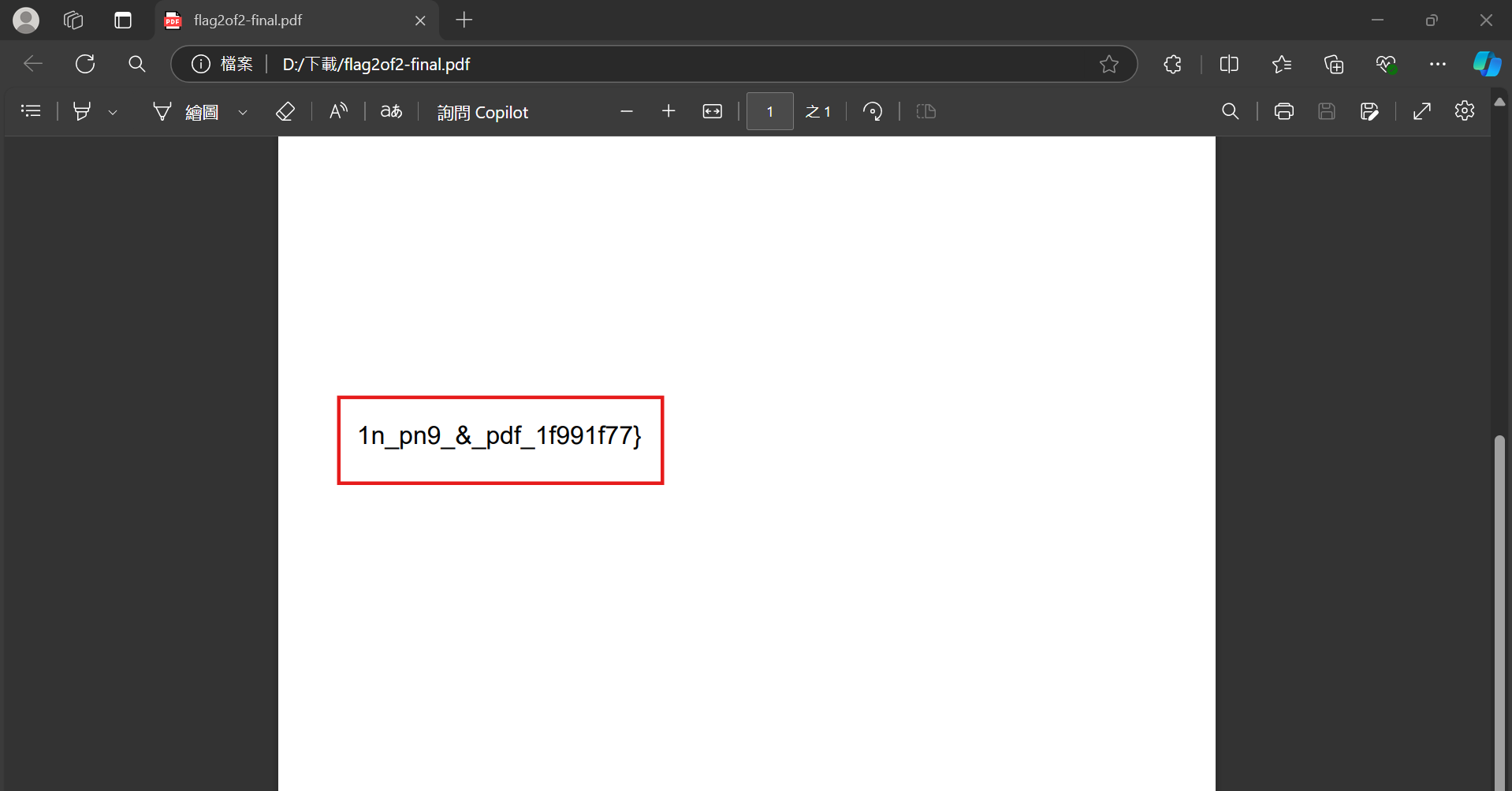
This question was given a PDF file, and after opening it, I found half of the Flag.
1n_pn9_&_pdf_1f991f77}Then use the command file flag2of2-final.pdf to check the file. Found that it is actually a PNG file. So we use mv flag2of2-final.pdf flag2of2-final.png to change the file name and open this picture.
picoCTF{f1u3n7_Finally, just combine the two.
picoCTF{f1u3n7_1n_pn9_&_pdf_1f991f77}#ScanSurprise
First use SSH to connect to the question.
ssh -p 51523 ctf-player@atlas.picoctf.netThen I found out that he gave me a QR Code picture called Flag.png. But because I don’t have a mobile phone at hand, I used zbarimg to extract the information.
zbarimg flag.pngWhat he outputs looks like this:
Connection Error (Failed to connect to socket /var/run/dbus/system_bus_socket: No such file or directory)
Connection Null
QR-Code:picoCTF{p33k_@_b00_b5ce2572}
scanned 1 barcode symbols from 1 images in 0 secondsSure enough, Flag came out!
picoCTF{p33k_@_b00_b5ce2572}






![[THM] Pwn101 Writeup](https://raw.githubusercontent.com/S1l3ntC0nquer/MyBlogPhotos/main/image/TryHackMe.jpg)








